
While the API Gateway is useful for providing a single entry point to your services, it is vulnerable to attack. In this chapter, you will learn how to secure the system from attackers using an HTTP(S) Load Balancer with an SSL/TLS certificate and Cloud Armor. Effectively, you will be building the wall (or more accurately, firewall) of the citadel to protect the application inside.
Note
The code for this chapter is in the citadel folder of the GitHub repository.
Securing from Attackers
In Chapter 9, you put services behind an API Gateway. In this chapter, you are going to protect them further.
Adding a Custom Domain
The Google API Gateway exposes a single URL to access the services behind the API. This is an HTTPS endpoint offering a secure connection. Similarly, putting the UI in a Cloud Storage bucket and exposing it as a website has provided a secure URL. However, it is more useful to put the API and the UI behind the same custom domain name. It is also useful to protect the API Gateway and UI behind a Global Load Balancer and provide your custom HTTPS URL with a valid SSL certificate. As part of Google’s global networking infrastructure, a Global Load Balancer also provides additional benefits such as high availability and scalability, optional caching via a global content delivery network (CDN), and protection against distributed denial-of-service (DDoS) attacks.
Setting up a Global Load Balancer has many steps, and you will work through them in this chapter.
There are many resources created in the chapter that need a name. Create an environment variable with a prefix (e.g., skillsmapper) to help keep names consistent:
export
PREFIX
=
skillsmapper
Reserving a Static IP Address
First, you need to reserve a static IP address for the Global Load Balancer. A static IP address remains consistent, so you can point a DNS entry at it and it will always be the same, as opposed to the default ephemeral IP address that can change.
While you are waiting for the certificate to be issued, you can continue to set up the load balancer.
Create a Load Balancer
To create a load balancer, there are several components you need to put into place in addition to the Cloud Run services and the API Gateway. Figure 11-1 shows the components you will create.
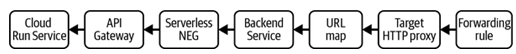
Figure 11-1. Overview of load balancer components
Work from left to right, starting from the API Gateway and working toward the forwarding rule. The forwarding rule will take the external IP address as input.
Network endpoint group
A network endpoint group (NEG) specifies a group of backend endpoints for a load balancer, as shown in Figure 11-2.

Figure 11-2. Serverless NEG
Note
At the time of writing, this is still a beta command, as the ability to create a serverless NEG backed by an API Gateway is relatively new; you will therefore need to include beta in the command.



